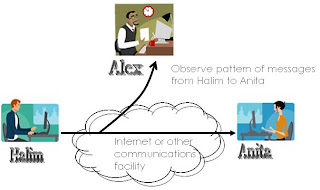
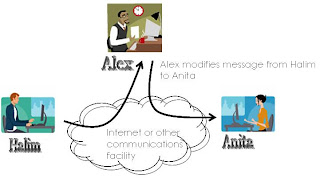
Cryptograpy Definition
Cryptography (or cryptology; from Greek κρυπτός, kryptos, "hidden, secret"; and γράφω, gráphō, "I write", or -λογία, -logia, respectively)[1] is the practice and study of hiding information. Modern cryptography intersects the disciplines of mathematics, computer science, and engineering. Applications of cryptography include ATM cards, computer passwords, and electronic commerce.(from //en.wikipedia.org/wiki/Cryptography).
Cryptograpy Concept
- scramble data in storage
- transmit data in to the Internet
- user can get the data but they can't read
Art of secret writing
i)
SteganographySteganography is the art and science of writing hidden messages in such a way that no one, apart from the sender and intended recipient, suspects the existence of the message, a form of security through obscurity. The word steganography is of Greek origin and means "concealed writing". The first recorded use of the term was in 1499 by Johannes Trithemius in his Steganographia, a treatise on cryptography and steganography disguised as a book on magic. Generally, messages will appear to be something else: images, articles, shopping lists, or some other covertext and, classically, the hidden message may be in invisible ink between the visible lines of a private letter.
The advantage of steganography, over cryptography alone, is that messages do not attract attention to themselves. Plainly visible encrypted messages—no matter how unbreakable—will arouse suspicion, and may in themselves be incriminating in countries where encryption is illegal.[1] Therefore, whereas cryptography protects the contents of a message, steganography can be said to protect both messages and communicating parties.
Steganography includes the concealment of information within computer files. In digital steganography, electronic communications may include steganographic coding inside of a transport layer, such as a document file, image file, program or protocol. Media files are ideal for steganographic transmission because of their large size. As a simple example, a sender might start with an innocuous image file and adjust the color of every 100th pixel to correspond to a letter in the alphabet, a change so subtle that someone not specifically looking for it is unlikely to notice it

Within this picture, the letters position of a hidden message are represented by increasing numbers (1 to 20), and a letter value is given by its intersection position in the grid. For instance, the first letter of the hidden message is at the intersection of 1 and 4. So, after a few tries, the first letter of the message seems to be the 14th letter of the alphabet; the last one (number 20) is the 5th letter of the alphabet.
Termonology Cryptograpycryptography referred almost exclusively to encryption, which is the process of converting ordinary information (plaintext) into unintelligible gibberish (i.e., ciphertext).[2] Decryption is the reverse, in other words, moving from the unintelligible ciphertext back to plaintext. A cipher (or cypher) is a pair of algorithms which create the encryption and the reversing decryption. The detailed operation of a cipher is controlled both by the algorithm and in each instance by a key. This is a secret parameter (ideally known only to the communicants) for a specific message exchange context. Keys are important, as ciphers without variable keys are trivially breakable and therefore less than useful for most purposes. Historically, ciphers were often used directly for encryption or decryption without additional procedures such as authentication or integrity checks.
plaintext - original message
ciphertext - coded message
cipher - algorithm for transforming plaintext to ciphertext
key - info used in cipher known only to sender/receiver
encipher (encrypt) - converting plaintext to ciphertext
decipher (decrypt) - recovering ciphertext from plaintext
cryptography - study of encryption principles/methods
cryptanalysis (codebreaking) - study of principles/ methods of deciphering ciphertext without knowing key
cryptology - field of both cryptography and cryptanalysis
CRYPTANALYSISDefinition of Crytanalysis
Cryptanalysis (from the Greek kryptós, "hidden", and analýein, "to loosen" or "to untie") is the study of methods for obtaining the meaning of encrypted information, without access to the secret information which is normally required to do so. Typically, this involves knowing how the system works and finding a secret key. In non-technical language, this is the practice of codebreaking or cracking the code, although these phrases also have a specialised technical meaning (see code).
"Cryptanalysis" is also used to refer to any attempt to circumvent the security of other types of cryptographic algorithms and protocols in general, and not just encryption. However, cryptanalysis usually excludes methods of attack that do not primarily target weaknesses in the actual cryptography, such as bribery, physical coercion, burglary, keystroke logging, and social engineering, although these types of attack are an important concern and are often more effective than traditional cryptanalysis.(from
)
Symmetric Algorithm
Symmetric-key algorithms are a class of algorithms for cryptography that use trivially related, often identical, cryptographic keys for both decryption and encryption.
The encryption key is trivially related to the decryption key, in that they may be identical or there is a simple transformation to go between the two keys. The keys, in practice, represent a shared secret between two or more parties that can be used to maintain a private information link.
Other terms for symmetric-key encryption are secret-key, single-key, shared-key, one-key, and private-key encryption. Use of the last and first terms can create ambiguity with similar terminology used in public-key cryptography.
 Example of Symmetric AlgorithmAssymmetric AlgorithmAssymmetric Algorithm
Example of Symmetric AlgorithmAssymmetric AlgorithmAssymmetric Algorithm cryptography is a cryptographic approach, employed by many cryptographic algorithms and cryptosystems, whose distinguishing characteristic is the use of asymmetric key algorithms instead of or in addition to symmetric key algorithms. Using the techniques of public key-private key cryptography, many methods of protecting communications or authenticating messages formerly unknown have become practical. They do not require a secure initial exchange of one or more secret keys as is required when using symmetric key algorithms. It can also be used to create digital signatures.
 Example of Assymmetric AlgorithmSymmetric Algorithm vs Assymmetric Algorithm
Example of Assymmetric AlgorithmSymmetric Algorithm vs Assymmetric Algorithm
This is a short comparisson of this 2 types of algorithm :
Speed of algorithmsSymmetric-key algorithms are generally much less computationally intensive than asymmetric key algorithms. In practice, asymmetric key algorithms are typically hundreds to thousands times slower than symmetric key algorithms.
Key managementOne disadvantage of symmetric-key algorithms is the requirement of a shared secret key, with one copy at each end. In order to ensure secure communications between everyone in a population of n people a total of n(n − 1)/2 keys are needed, which is the total number of possible communication channels.[1] To limit the impact of a potential discovery by a cryptographic adversary, they should be changed regularly and kept secure during distribution and in service. The process of selecting, distributing and storing keys is known as key management, and is difficult to achieve reliably and securely.
Hybrid cryptosystemIn modern cryptosystems designs, both asymmetric (public key) and symmetric algorithms are used to take advantage of the virtues of both. Asymmetric algorithms are used to distribute symmetric-keys at the start of a session. Once a symmetric key is known to all parties of the session, faster symmetric-key algorithms using that key can be used to encrypt the remainder of the session. This simplifies the key distribution problem, because asymmetric keys only have to be distributed authentically, whereas symmetric keys need to be distributed in an authentic and confidential manner.
Systems that use such a hybrid approach include SSL, PGP, GPG etc.
Caesar Ciphers Caesar cipher
Caesar cipher also known as a Caesar's cipher, the shift cipher, Caesar's code or Caesar shift, is one of the simplest and most widely known encryption techniques. It is a type of substitution cipher in which each letter in the plaintext is replaced by a letter some fixed number of positions down the alphabet. For example, with a shift of 3, A would be replaced by D, B would become E, and so on. The method is named after Julius Caesar, who used it to communicate with his generals.
The encryption step performed by a Caesar cipher is often incorporated as part of more complex schemes, such as the Vigenère cipher, and still has modern application in the ROT13 system. As with all single alphabet substitution ciphers, the Caesar cipher is easily broken and in practice offers essentially no communication security.
Examples :Using this system, the keyword "zebras" gives us the following alphabets:
Plaintext alphabet: abcdefghijklmnopqrstuvwxyz
Ciphertext alphabet: ZEBRASCDFGHIJKLMNOPQTUVWXY
A message of :flee at once. we are discovered!
enciphers toSIAA ZQ LKBA. VA ZOA RFPBLUAOAR!
 ROT13 is a Caesar cipher, a type of substitution cipher. In ROT13, the alphabet is rotated 13 steps
ROT13 is a Caesar cipher, a type of substitution cipher. In ROT13, the alphabet is rotated 13 steps.
Vigenere CiphersThe
Vigenère cipher is a method of encrypting alphabetic text by using a series of different Caesar ciphers based on the letters of a keyword. It is a simple form of polyalphabetic substitution.
The Vigenère (French pronunciation: [viʒnɛːʁ]) cipher has been reinvented many times. The method was originally described by
Giovan Battista Bellaso in his 1553 book La cifra del. Sig. Giovan Battista Bellaso; however, the scheme was later misattributed to Blaise de Vigenère in the 19th century, and is now widely known as the
"Vigenère cipher".
This cipher is well known because while it is easy to understand and implement, it often appears to beginners to be unbreakable; this earned it the description le chiffre indéchiffrable (French for 'the unbreakable cipher'). Consequently, many people have tried to implement encryption schemes that are essentially Vigenère ciphers, only to have them broken.
 Vinegere Tableau
Vinegere TableauFor example, suppose that the plaintext to be encrypted is:
ATTACKATDAWNThe person sending the message chooses a keyword and repeats it until it matches the length of the plaintext, for example, the keyword "LEMON":
LEMONLEMONLEThe first letter of the plaintext, A, is enciphered using the alphabet in row L, which is the first letter of the key. This is done by looking at the letter in row L and column A of the Vigenère square, namely L. Similarly, for the second letter of the plaintext, the second letter of the key is used; the letter at row E and column T is X. The rest of the plaintext is enciphered in a similar fashion:
- Plaintext : ATTACKATDAWN
- Key : LEMONLEMONLE
- Ciphertext: LXFOPVEFRNHR