Salam semua ...Ok, macam biasa ..kalau dh nama pun 1st class nih kami telah diterangkan secara ringkas mengenai modul Network Security ni. Pensyarah untuk modul ini adalah En. Zaki bin Mas'ud (email : zaki.masud@utem.edu.my)
Modul ini merangkumi 14 tajuk yang merangkumi :
- ¡Introduction to Information Security
- ¡Introduction to Cryptography
- ¡Modern Cryptography
- ¡Access Control and Authentication
- ¡Program Security
- ¡Database Security
- ¡Security in Networks
- ¡Security in Applications
- ¡Firewall
- ¡Intrusion Detection System
- ¡Wireless Security
- ¡Legal and Ethical Issues in Computer Security
- ¡Cyberlaws
- ¡Administering Security
First class juga kami telah diuji dengan 1st quiz dimana En. Zaki ingin menguji tahap pemahaman & apa yang para pelajar tau tentang serba sedikit mengenai Network Security ini.. haha ..
Serba sedikit review tentang pembelajaran yang pertama :
WHAT IS SECURITY ?
- Security is a quality or state of being secure that is to be free from danger.
- To be protected from adversaries.
SECURITY PRINCIPLE ?
It have 3 types including :
- Confidentially - prevention of unauthorized disclosure of information
- Integrity - prevent of unauthorized modification of information
- Availability - unauthorized withholding of information or resources
- Threat : A potential for violation of security, which exists when there is a circumstance,capability,action, or event that could breach security & cause harm. That is,a threat is a possible danger that might exploit vulnerability
- Attack : An assault on system that derives from an intelligent threat,that is an intelligent act that is a deliberate attempt (especially in the sense of method or technique) to evade security services & violate the security policy of a system.
- Task 1 : VMware Workstation Installation
- Task 2 : 1.Creating Disk Image
- Task 3 : Installing Windows Server 2003 on Virtual Machine
SECURITY TRENDS ? (refer picture below)

THREAT & ATTACK
Passive Attack : eavesdropping on, or monitoring of, transmissions.
The Goal : to obtain information that is being transmitted.
Types : release of message contents & traffic analysis
Release of message contents
eassily understood. A telephone conversation, an electronic mail message, and a transfered file may contain sensitive or confidential information (refer picture below)

Traffic analysis
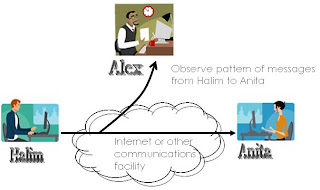
Is subtler, which suppose that we had a way of masking the contents of message or other information traffic so that opponents, even if they captured the message, could not extract the information from the message. The common technique for masking contents is encryption. If we had encryption protection in place, an opponent might still be able to observe the patern of these message. The opponent could determine the location & identity of communicating hosts and could observe the frequency and length of messages being exchanged(refer picture below)
Active Attacks : involve some modification of the data stream or the creation of a false stream & can be subdivided into 4 categories :masquerade, replay, modification of message, & denial of service.
Masquerade
takes place when one entity pretends to be a diffrent entity.(refer picture below)

Replay
involve the passive capture of a data unit and its subsequent retransmission to produce an unauthorized effect (refer picture below)

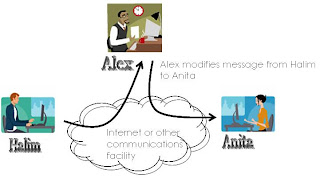
Modification of messages
some portion of a legitimate message is altered, or that message are delayed or reordered, to produce an unauthorized effect.(refer picture below)
Denial of service
prevents or inhibits the normal use or management of communication facilities.(refer picture below)


SECURITY SERVICE
X.800 defines a security service as a service provided by a protocol layer of communicating open systems, which ensures adequate security of the system or of data transfers.
RFC 2828 define which provides the following definitions : a processing or communication service that is provided by a system to give a specific kind of protection to system resources.
5 Categories & 14 Specific Services

SECURITY MECHANISM
Any process (or a device incorporating such a process) that is designed to detect, prevent or recover from a security attack.
Specific Security Mechanism

Pervasive Security Mechanism


LAB 1.::Introduction to Virtualization & VMware::.
Virtual Machines (VM) allow you to run any operating system in a new window. This is done by using virtualization, which is the general technology used by virtual machines. Imagine what you could do if you had under your control many computers, possibly connected together. Best is, they are simple to use and have only little performance hit. Well see what those applications can do, how they can help you (test any OS or application while keeping you PC clean), and how to use them. Further, VM make it possible to create testing plateforms for your applications, websites, or virtually anything!
: 2.To know how to get the virtual machine console
